Use SAML or OIDC authentication
The example in this topic illustrates how to display an embedded dashboard using SAML authentication. The same code works for OIDC except the loginMode parameter.
A live example can be seen on GitHub. Also check out other examples.
The workflow
Here is the workflow of the example.
-
Client Application checks if auth token is still valid. If yes, jumps to Step 4.
-
Client Application opens the Library Web login page (
https://[Your Strategy Environment]/MicroStrategyLibrary/auth/login-dialog.jsp) in a new tab. The login page will be responsible for showing a login dialog. -
After the user finishes logging in, the login page will send a JavaScript message to inform the Client Application.
-
The Client Application gets the message, fetches the auth token, and uses it to make REST API calls or uses it in Strategy’s Embedding SDK.
You may encounter some difficulties in this workflow:
- The Library Web login page couldn't be opened in a new tab.
- This might be caused by your Chrome site settings doesn't allow pop-ups.
- In this case, you will see an icon on the right of location bar, which notifies you the pop-ups are blocked:
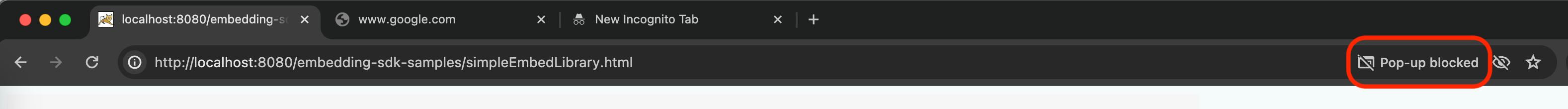 You need to unblock the pop-ups like this:
You need to unblock the pop-ups like this:
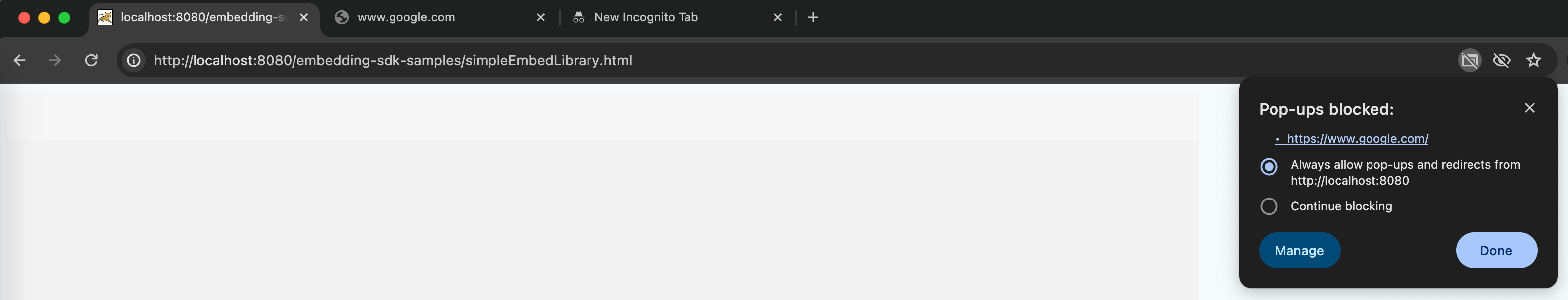
- The user finishes logging in, but the Client Application doesn't proceed. The Library Web login page isn't closed and the embeded dossier doesn't show.
- This might be caused by your strict CSP settings. If your COOP(Cross-Origin-Opener-Policy) setting is same-origin, the Library Web login page can't get the Client Application window so can't send messages to it.
- In this case, you need to change your COOP setting to unsafe-none, which is the default value. Then the login process will work.
For MicroStrategy ONE June 2024 or after
In MicroStrategy ONE June 2024, we add the partitioned cookie change to enable the customer to use the Embedding SDK even if third-party cookies are blocked. But if third-party cookies are blocked, the old SAML or OIDC login process can't work.
You can unblock the third-party cookies manually to support the old workflow, but we recommend you use the new embedding auth APIs, which can work in the third-party cookies blocked case, and simplify the SAML or OIDC login logic. You can see the examples in the playground. A simple code piece would be like this:
microstrategy.embeddingContexts.embedLibraryPage({
serverUrl: "{YOUR_LIBRARY_SERVER_URL}",
placeholder: document.getElementById("LibraryHomePageContainer"),
enableCustomAuthentication: true,
customAuthenticationType: microstrategy.dossier.CustomAuthenticationType.AUTH_TOKEN,
getLoginToken: () => microstrategy.auth.samlLogin("{YOUR_LIBRARY_SERVER_URL}"),
});
The new API microstrategy.auth.samlLogin(serverUrl) or microstrategy.auth.oidcLogin(serverUrl) creates an identity token to share the sessions, so you must ensure you have a secret key to create identity tokens first. You can check it in the Library settings here:
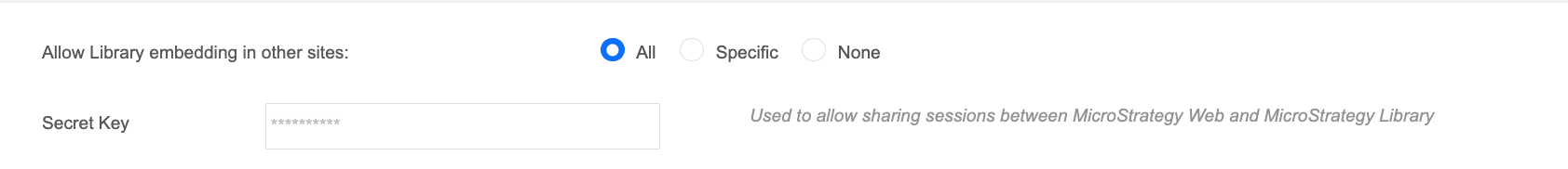
The secret key must have its content here.